Here is what happened. I copied entire WordPress folders to a new domain’s site root. I always do this instead of installing everything from fresh. It saves a lot of time.
I activated all the plugins and while I was changing the Google Analyticator’s settings, I found that it is affected with Malware?
First I thought it might be my theme files so I did a Google search to find if there are any issues with Google Analyticator and Malware. I could see few posts in forums suggesting that Google Analyticator does indeed somehow is affected with Malware or at least the malicious code uses Google Analyticator to spread Malware.
However it might not be the case as Ronald Hoff’s post suggests.
When you are in Google Analyticator’s settings and click on Save, either it redirects to Google’s home page or you get a malware warning in the browser.
Also the affected website shows following warning:
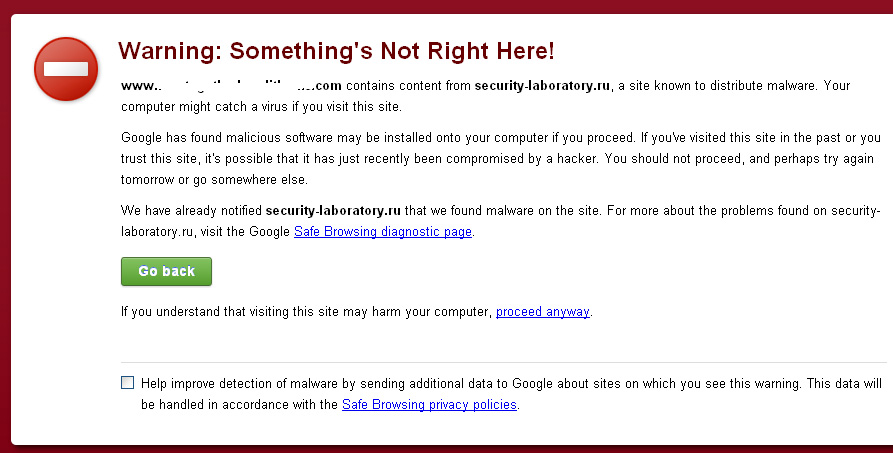
The problematic url is security-laboratory.ru which is notorious for injecting malware in free open source scripts specially in osCommerce. I’ve seen this Malware in some of osComemrce sites and it is pretty nasty. This is the first time that I see it in a WordPress site.
The nasty stuff about security-laboratory.ru is that it doesn’t just add a code in the files which can be easily found in the php files but in adds an eval code which is hard to find.
It affects the header, footer, index and plenty of other common php files in osCommerce and also modifies .htaccess in very clever way. In .htaccess it adds malicious code towards the end by adding many empty lines before. So if open .htaccess file in a text editor you might not see code after the end of normal code but just scroll down and then you will discover the malicious codes.
I disabled the plugin and the malware was no longer seen.
I quickly checked some of other WordPress sites and I didn’t find this issue.
There is a chance that there is malicious code in the files.
I tried to backtrack what has happened. There might be chances that I visited a security-laboratory.ru malware affected website and then I Installed WordPress on this new site. Everything was fine until I tried to update the settings for Google Analyticator and at that point of time the WordPress site might be affected with Malware.
Before Google Analyticator I also changed the settings for various other plugins but I didn’t see any Malware warnings.
Checking the files for malicious code
I did a thorough search by searching for eval( string in all files in WordPress installation and guess what, I found that some files are affected.
There is file in the site root – tmp_1407122956494849.php which contains a piece of jumbled up code and it looks all too familiar.
So it seems Malware has affected the WordPress site.
.htaccess file
As usual I also find bunch of malicious code in .htaccess.
There were a bunch of lines with Error redirect to plasticspark.ru after the normal WordPress .htaccess entries.
Next I did a search for tmp_ files from webhosting root to make sure that non of other sites are affected. The command to search for a file with tmp_ name in it is
find /home/*/public_html/ -name ‘tmp_’
Then another search for entries in .htaccess
find /home/*/public_html/.htaccess -exec grep “plasticspark.ru” ‘{}’ /dev/null \; -print
Nothing found so I can be assured that other sites are not affected.
Conclusion
To conclude I can assume that the malicious code might have been injected to this new WordPress site when I was setting it up after visiting any other malware affected sites.
Now the most important question is how this code was injected into the WordPress? Is WordPress prone to such injection or it was the Google Analyticator plugin which gave way to the malware into WordPress?
Here are some safety tips
When you see the warning in browser for a malware then never ever visit the website.
If you visit a malware affected site then chances are that your computer might get affected as well.
Leave a Reply